OutSystems Development Cloud (ODC) counts on a resourceful mechanism to manage user accounts, both technical and end-user. The /Users did its job in the previous version, O11, but it lacked significant support for common user handling flows, such as an intuitive onboarding process and robust multi-tenancy handling.
This time around OutSystems has nailed it. The new users management engine is not only natively cloud-based, but it also features a clever design. It has some automation aspects that will accelerate the delivery of apps built on the new platform bringing it to another level. So, if you are a dinosaur like me wrapping your head around the new toy or a newbie trying to figure out the cool stuff in this new product, here are 6 reasons why you will love it:
1 Everything, all in one place
The all-new ODC Portal centralises the management of all the identities across apps and environments (or stages) in 1 place. Be it an end-user that will need to be given the approvers role in order to approve and reject sales orders in a CRM app or a new developer that will be provided with an IT account to get coding.
It is all now managed seamlessly in this one interface, the ODC Portal. The same credentials will be used to get access to apps across all the environments. And the user account can have different privileges depending on the environment.
For the veterans, this means we don’t need to go to Lifetime if we want to manage developer accounts or go to the environment-specific /Users app if we need to manage roles and permissions for an app.
2 No more 3rd party password definition
For veteran IT admins, ODC means a massive improvement in how credentials are securely managed as they will be defined by the account holders themselves, not by an admin, to then be manually handed over to the individual. This means no more ‘123456’ or ‘changeit123’ kinds of passwords. I’ve seen that being done a couple of times.
For developers transitioning from O11 into ODC, this means we no longer need to build repetitive user management modules. This is a great time saver and will get clients closer to delivery quicker.
3 Roles are clearer and on point
With ODC, one can be either a member, an old IT account, and/or an end-user. If they are a member, they are either an Administrator, a Developer, or a QA. This is to start with, and it will cover 80% of the cases in any Factory where most of the member users are supposed to be Developers. With the use of organisational roles, flexibility is brought to a whole new level, and it will be explored in the next topic.
Now, as for end-users, all the good practices that O11 observed are still available. App-specific roles are defined in design time. They can be grouped into end-user groups by an IT admin at the environment level. And users’ access is granted or revoked across stages within the portal.
Programmatically, nothing changes in terms of checking, granting or revoking roles to end-users. The good old Check, Grant and Revoke services are still available on both the server and client sides.
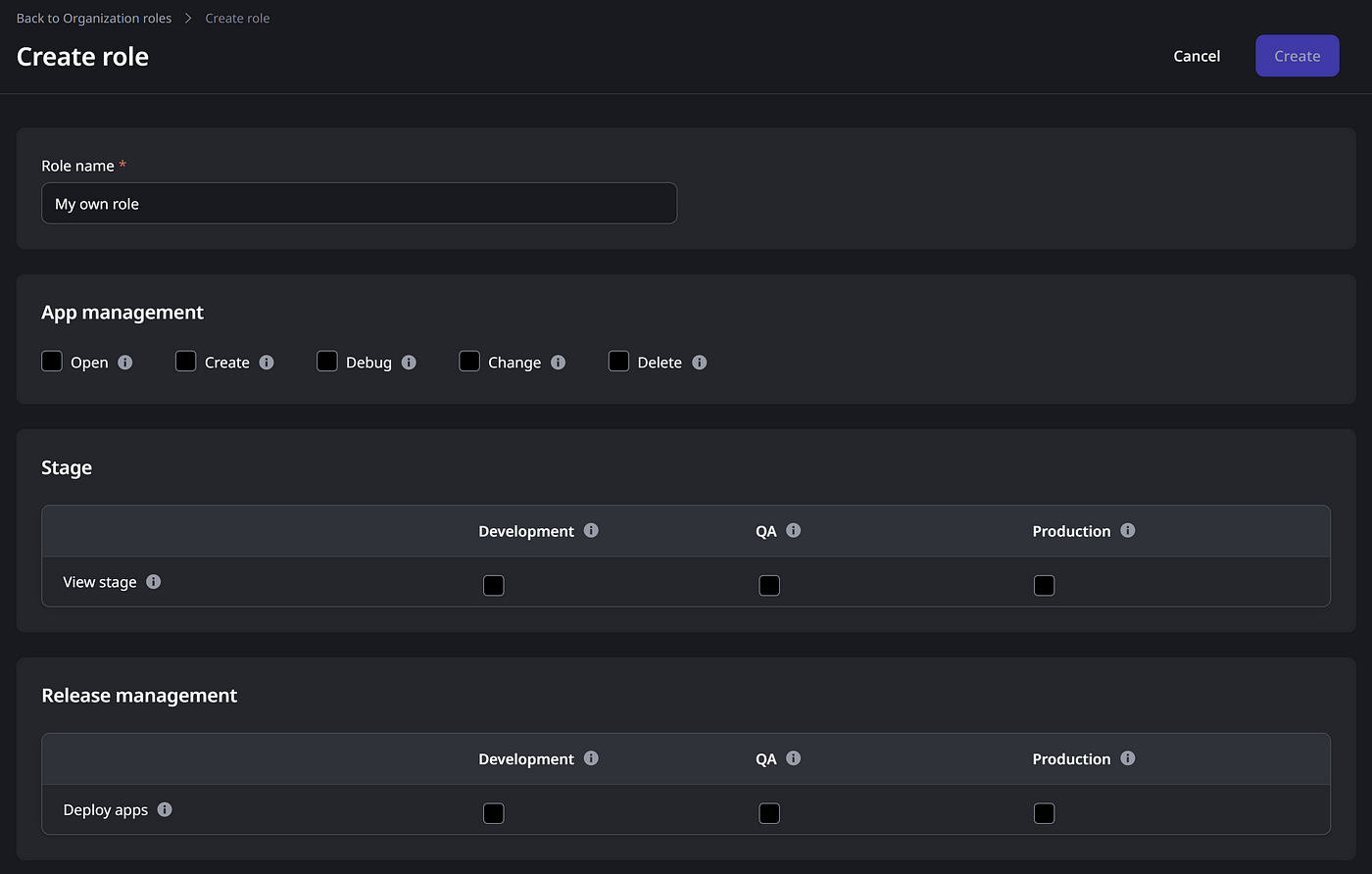
4 Organisation roles
The administrator now has the option to customise and manage privileged access to multiple components across the infrastructure via a slick interface. It is quite clever and user-centred, the way the categories for members are laid out.
The 5 levels of app management, Open, Create, Debug, Change and Delete, are pretty much all you can do in terms of managing apps. And they make much more sense now, rather than before in Lifetime, where these same roles are defined in levels, which brings an unnecessary hierarchical aspect to it.
Staging and release management have their own grouped access roles. Besides, other key aspects of infrastructure management have their own groups, such as Monitoring, Configurations, Connections, and Users Management. Even Forge and visibility to Support Cases can be managed here.
5 Accelerators for end-user self-registration flow
Apps now on ODC are scaffolded with a pre-defined self-registration flow. End-users can use this flow in order to request their own password reset link in a typical “forgot my password” flow. And the logic behind it is already connected with the one portal.
These kinds of features are also common to find in the Forge and are provided as-is by community members or partners. Check out some of the components that deliver similar functionality on O11. With these pre-built accelerators in ODC, it means less coding for these mundane activities.
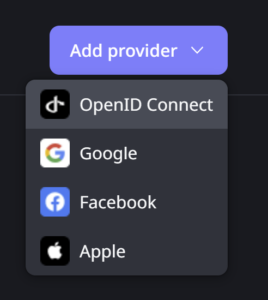
6 External identity providers are a few clicks away
Another recurrent requirement that is now accelerating immensely is the embedding of authentication against external identity providers such as social networks or other trusted identity providers. With ODC, this capability can be added to an app with just a few configuration steps in a no-code approach, with less reliance on coding.
Besides, it guarantees the implementation is standardised, which reduces operational costs in terms of maintenance and support and brings it into the realm of the OutSystems Cloud support. Which adds an additional layer of reliability, especially for enterprise-grade customers.
All in all
The product is in its early stages of GA (General Availability). And, despite the fact that it still lacks some useful features, like this one, it was designed with robust mechanisms from scratch. Which is promising. I will not be surprised if this article is outdated a few days after being published.
Reference
OutSystems: User Management
OutSystems: Secure your app with end-user roles
OutSystems: Self-registration flow
OutSystems: Create a screen for users to self-register
About the author

Joao Melo, Head of Digital Products | Principal Tech Lead | OutSystems MVP
He has worked in the software industry for over 20 years, including roles as a Software Developer, Product Owner, Solution Architect and Tech Lead. He has helped companies achieve results with a pragmatic approach to software development. An OutSystems MVP for over 7 years, Joao is the Head of Product Delivery at PhoenixDX, the builder of Hubway Connect.
This article was originally published on Medium






